With mobile apps everywhere, security threats are on the rise. In 2023, mobile cyberattacks targeted millions of users with scams like smishing and malware. Smishing, by the way, where scammers use fake texts to lure users into clicking bad links or sharing personal info, isn’t just an issue for casual users. 75% of IT pros and organizations reported smishing attempts, too.
To make matters more serious, early 2024 saw AdWare and RiskTool lead as the most common types of mobile malware worldwide, with Trojan malware accounting for 11% of all attacks. But securing your apps and data doesn’t have to be complicated.
In this guide:
- We’ll cover the essentials of securing mobile apps and the most important mobile app security requirements.
- We’ll discuss common risks and the latest threats to user data security in highly regulated industries.
- We’ll find out everything about how to prepare a mobile app security test and how to ensure mobile app security.
- We’ll talk about simple strategies to secure mobile applications.
With practical tips and insights, you’ll feel prepared to keep your mobile experience safe and secure, no matter what new scams are out there. Let’s go!
Mobile App Security in Regulated Industries
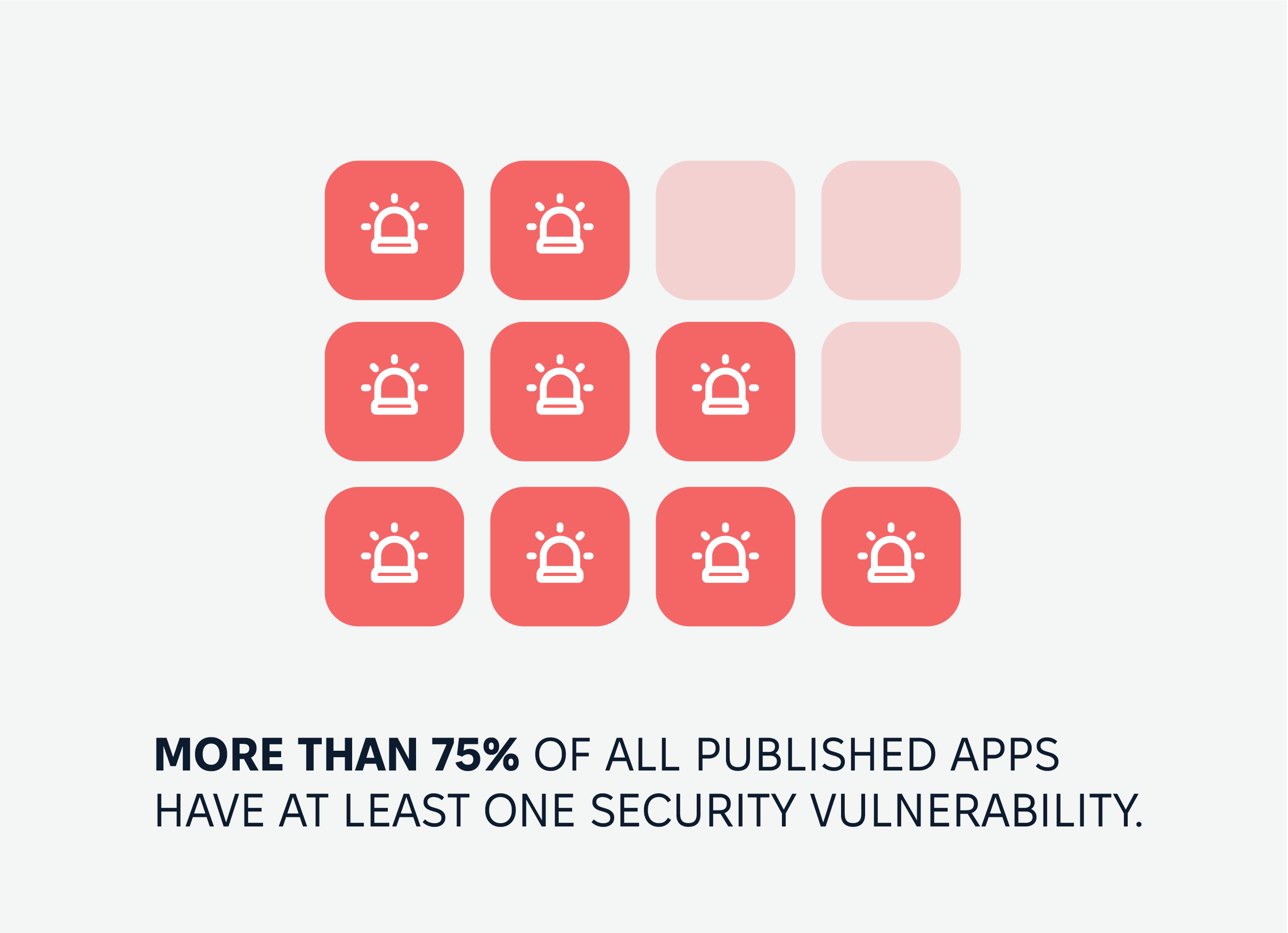
Statistics show that more than 75% of all published apps have at least one security vulnerability.
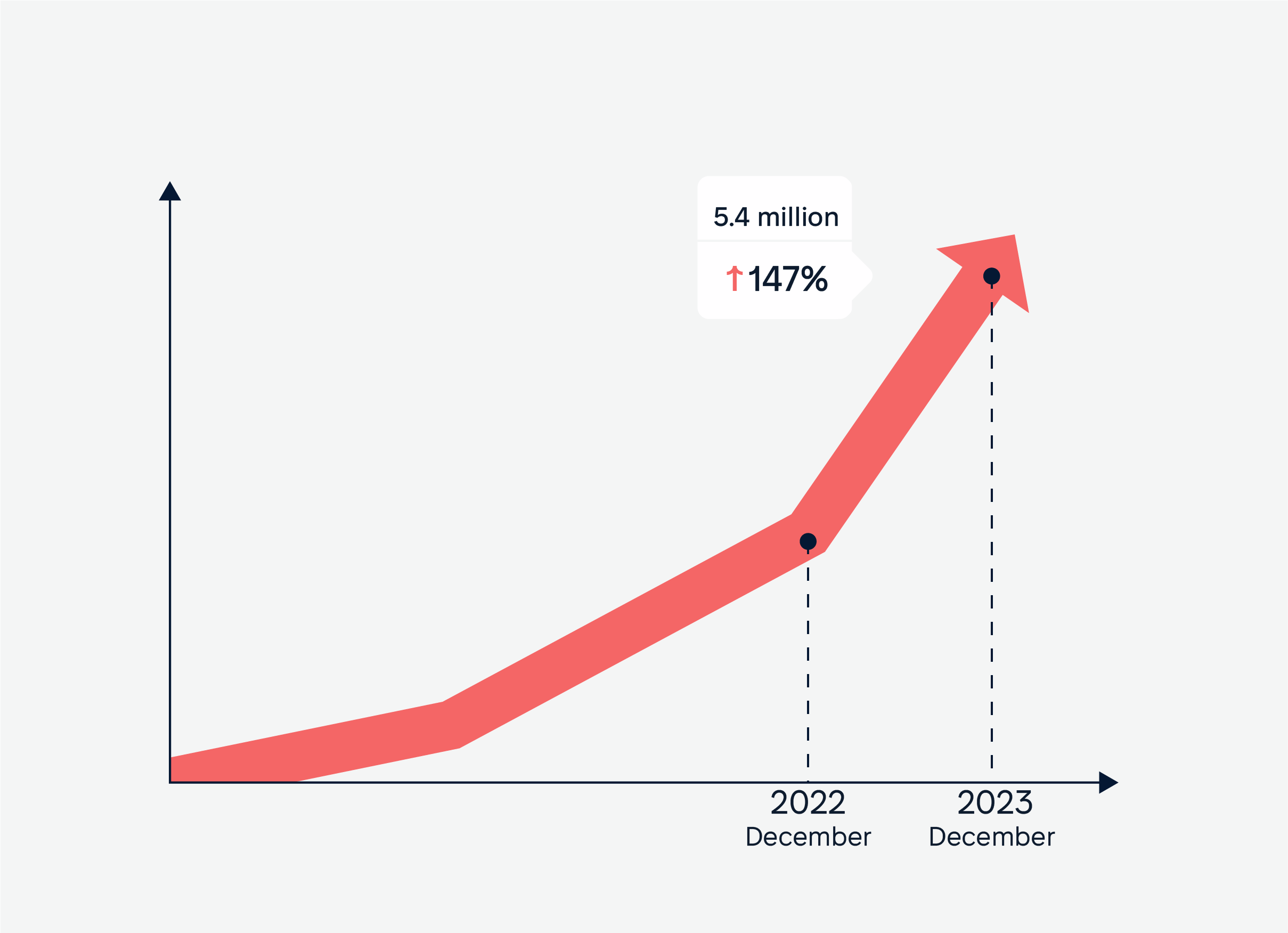
In December 2023, global mobile cyberattacks reached approximately 5.4 million, marking a 147% increase from December 2022.
For industries like healthcare, finance, and insurance, there’s a lot more at stake than an average app. They handle patient information, financial records, and personal data that must be safeguarded by law. That means these apps need extra layers of security, from strong walls to watchful guards, to keep out threats and prevent leaks.
Challenges and data breaches’ implications
Every regulated industry has its own set of security challenges. For healthcare, it’s about safeguarding patient records under HIPAA. Financial services have to follow PCI DSS rules to protect payment information. Insurance companies must comply with data privacy regulations that demand strict security. One wrong move and organizations face hefty fines, legal trouble, and loss of trust.
One of the examples is the 2020 Blackbaud breach, which exposed data from healthcare to education. The company informed authorities of a data security incident involving a ransomware attack, affecting nonprofit organizations nationwide. Despite the security experts intervening to prevent system access from being fully blocked and encrypted, a backup file containing personal information such as names, addresses, contact details, birth dates, and demographic data related to relationships with the Oregon Tech Foundation was accessed and removed.
Another illustrative case is a massive breach at National Public Data (NPD) in early 2024 that compromised 2.9 billion records, making it one of the largest data leaks in recent history. The data, including full names, addresses, dates of birth, and Social Security numbers, impacted nearly half of the world’s population. This breach has raised global concerns over data security practices, highlighting the necessity for robust protection of such large-scale personal information repositories.
The Basics: Essential Mobile App Security Requirements
Let’s take a closer look at the building blocks of mobile app security requirements that protect sensitive information.
The core elements of mobile app security
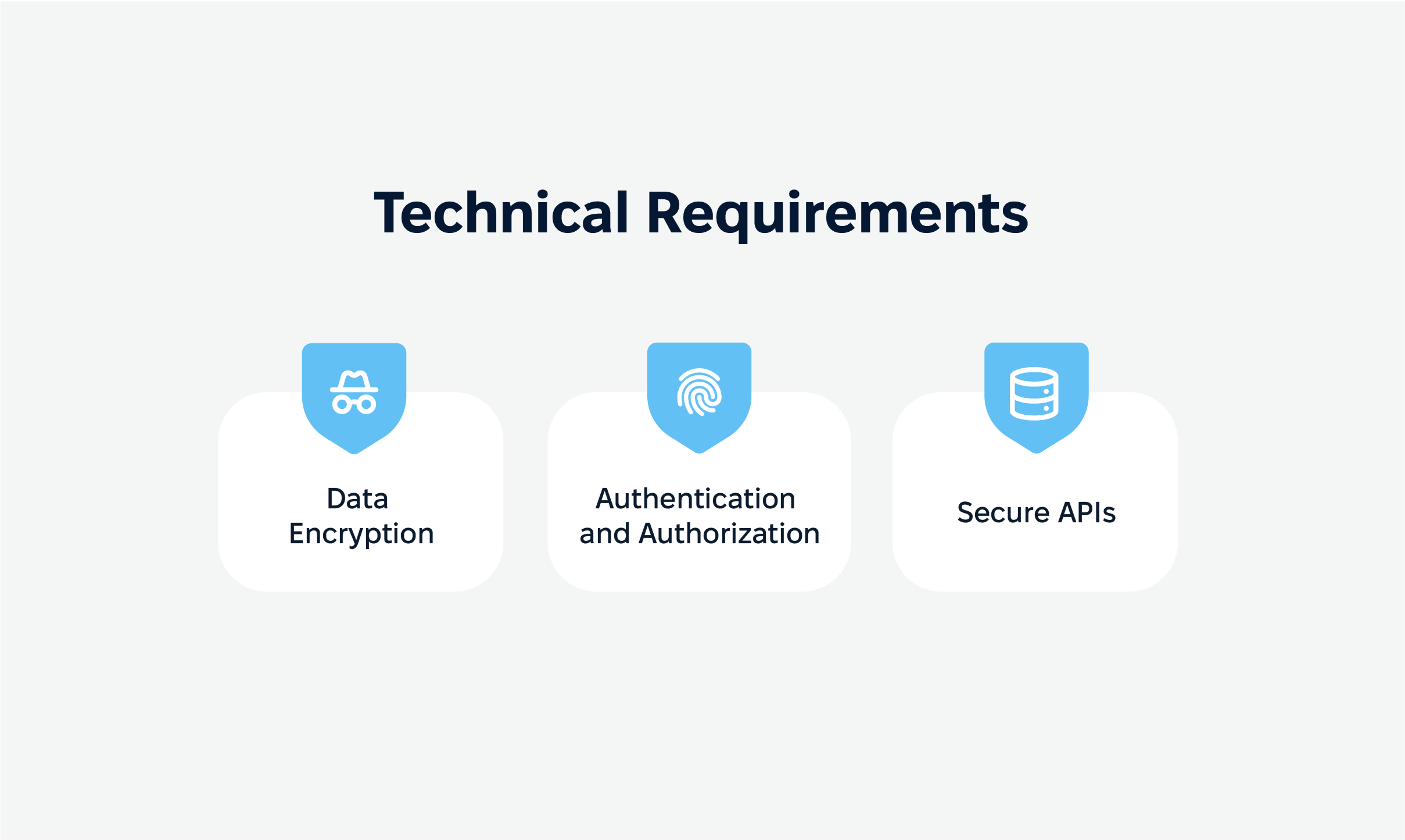
Data encryption
Think of data encryption as locking private data in an unbreakable safe. Encryption ensures that all data, whether it’s actively being transferred or just sitting in storage, is scrambled and unreadable to anyone who doesn’t have the right key.
Encryption algorithms like AES-256 offer robust protection against cybercriminals, making sure that even if they intercept the data, it’s useless without the decryption key.
Authentication and authorization
Only the right people should have access to an app’s sensitive areas, and that’s where authentication and authorization come in.
Authentication is all about verifying that a user is who they say they are. Multi-factor authentication (MFA) adds another layer, requiring a second verification step, like a one-time code sent to a mobile device.
Authorization, on the other hand, ensures that users only access the parts of the app they’re meant to. This is the app’s way of making sure that each user has the correct “clearance” to see what they’re seeing.
Secure APIs
APIs (Application Programming Interfaces) are like gates between different parts of an application and the internet, where data flows in and out. However, without proper security, these doors can become easy entry points for hackers.
Secure APIs require strict authentication, authorization, and validation to make sure that only authorized users and services access them, keeping data safe from unauthorized access.
Technical requirements: building a strong foundation
While the core elements of security help keep your app safe at a high level, certain technical implementations create the infrastructure for real security. These are non-negotiable for regulated industries.
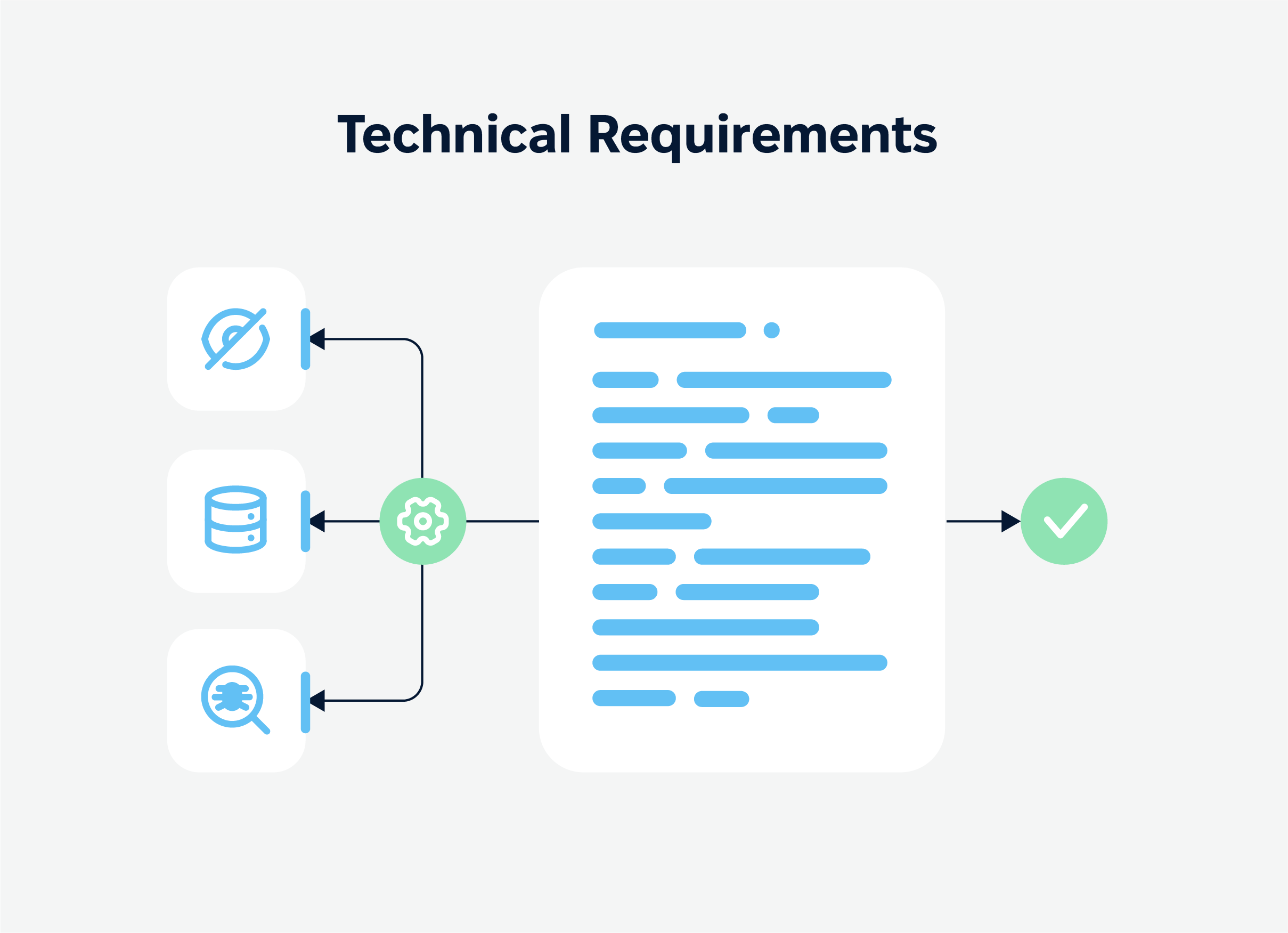
- Code obfuscation. It rearranges and obscures code structure to make it nearly impossible for hackers to reverse-engineer or understand. This extra layer of protection makes it harder for anyone who does get access to figure out the app’s inner workings.
- Secure data storage. If mobile devices must store sensitive user data, they should use encrypted storage methods, ensuring data is unreadable without proper decryption. Secure storage is especially important for healthcare and finance apps, which might hold patient records or financial transactions that need the utmost protection.
- Vulnerability management. Apps change over time, with regular updates and new features added to meet user needs. Vulnerability management is the practice of scanning an app for security weaknesses regularly and patching them before they become real issues.
Mobile app security standards and best practices
Following industry-recognized standards and best practices helps ensure that your mobile app security requirements align with broader, accepted norms. Here are the most important mobile app development standards.
OWASP Mobile Security Project
OWASP provides a comprehensive guide on mobile security best practices. It includes a regularly updated list of the top mobile security risks, with advice on how to address each one, making it a crucial resource for development teams.
The National Institute of Standards and Technology guidelines
They are essential for any app handling sensitive information. This is a detailed framework for managing mobile app security and privacy risks, emphasizing everything from encryption practices to secure network communications.
ISO/IEC 27001
This is a global standard for information security management, helping organizations handle sensitive info systematically and effectively. Compliance with ISO/IEC 27001 demonstrates a commitment to data protection, adding credibility and reassuring users that their data is in safe hands.
Industry-Specific Compliance Requirements
Different industries have specific mobile app compliance requirements to protect the kinds of personal data they handle. In regulated industries, these requirements are a critical part of mobile app security.
Why are these requirements so important? First of all, not meeting them could lead to fines, lawsuits, and loss of business. Here’s how some key industries manage their unique compliance needs.
Healthcare: HIPAA compliant mobile app
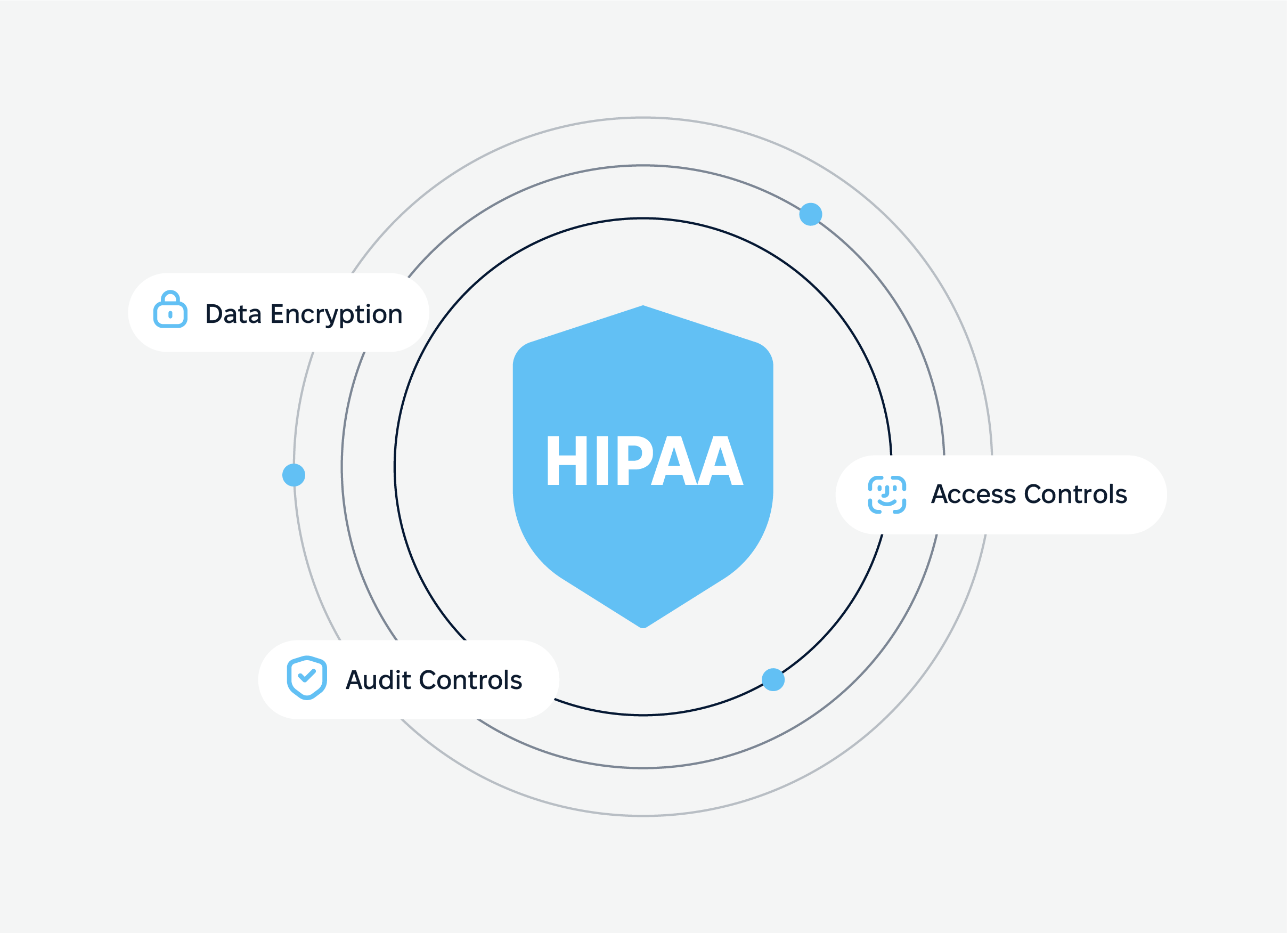
For healthcare providers, meeting Health Insurance Portability and Accountability Act requirements is essential for protecting patient data. HIPAA compliant mobile app uses strict controls around who can view, transfer, and store health-related information. Here’s what it entails:
- Data encryption. All Protected Health Information (PHI) must be encrypted at every point in its lifecycle, whether it’s being stored on a device or transmitted across a network.
- Access controls. They ensure that only authorized healthcare providers can access this data while unauthorized users are kept out.
- Audit controls. HIPAA requires organizations to maintain logs of all data access activities. These logs, or audit trails, can be reviewed to spot suspicious activity and prove compliance if questioned.
See how we achieved healthcare compliance requirements in building the Mental Health Support App
Financial industry requirements: PCI DSS
The financial industry faces unique mobile app compliance requirements to protect payment data and other sensitive financial information. The main security guideline here is the Payment Card Industry Data Security Standard (PCI DSS). It includes:
- Data masking. To protect sensitive financial data, information like credit card numbers are “masked,” meaning they are only partially shown, protecting them from unauthorized viewers.
- Secure network requirements. Mobile apps in financial services must secure their networks to prevent data breaches, including using firewalls, encryption, and intrusion detection systems.
- Continuous monitoring to quickly detect and respond to potential threats. It ensures there are no gaps in security, keeping user data safe.
Insurance apps: GDPR and GLBA
Insurance providers handle sensitive personal data, and they must comply with data privacy regulations like GDPR (General Data Protection Regulation) and the GLBA (Gramm-Leach-Bliley Act). Here’s what that entails:
- Only collect the data that are absolutely necessary for a service. If a user is getting an insurance quote, only the relevant information should be requested, and nothing more.
- GDPR requires apps to get clear, explicit consent from users before collecting personal information. This means users are fully aware of and have agreed to data collection and usage terms.
- Under GDPR, users have the right to access their data and even request deletion if they choose. Insurance companies must be prepared to fulfill these requests in a timely manner.
Cross-industry requirements
Certain standards are beneficial across industries, regardless of their specific requirements. These include SOC 2 and ISO 27001:
- SOC 2. A widely recognized standard for data security and privacy. It ensures that customer data is managed in a secure and reliable manner. Following SOC 2 can add a significant trust factor for apps handling any sensitive data.
- ISO 27001. A global standard for managing information security. It helps organizations develop a thorough, structured approach to protecting sensitive information, from risk assessment to incident response.
Establishing these mobile app security requirements may seem like a daunting task, but it’s crucial for protecting sensitive users’ data, ensuring regulatory compliance, and, most importantly, building a foundation of trust with users and stakeholders.
Our experts will analyze your app’s security needs and provide a detailed compliance roadmap. Book a free 30-minute consultation now.
Mobile App Security Testing Guide
Mobile application security testing is a fundamental part of the app development lifecycle. The goal? Spot vulnerabilities and weaknesses before real threats do.
Main testing methodologies
The right testing approach can make or break your security efforts. Here are the core methodologies for mobile application security testing.
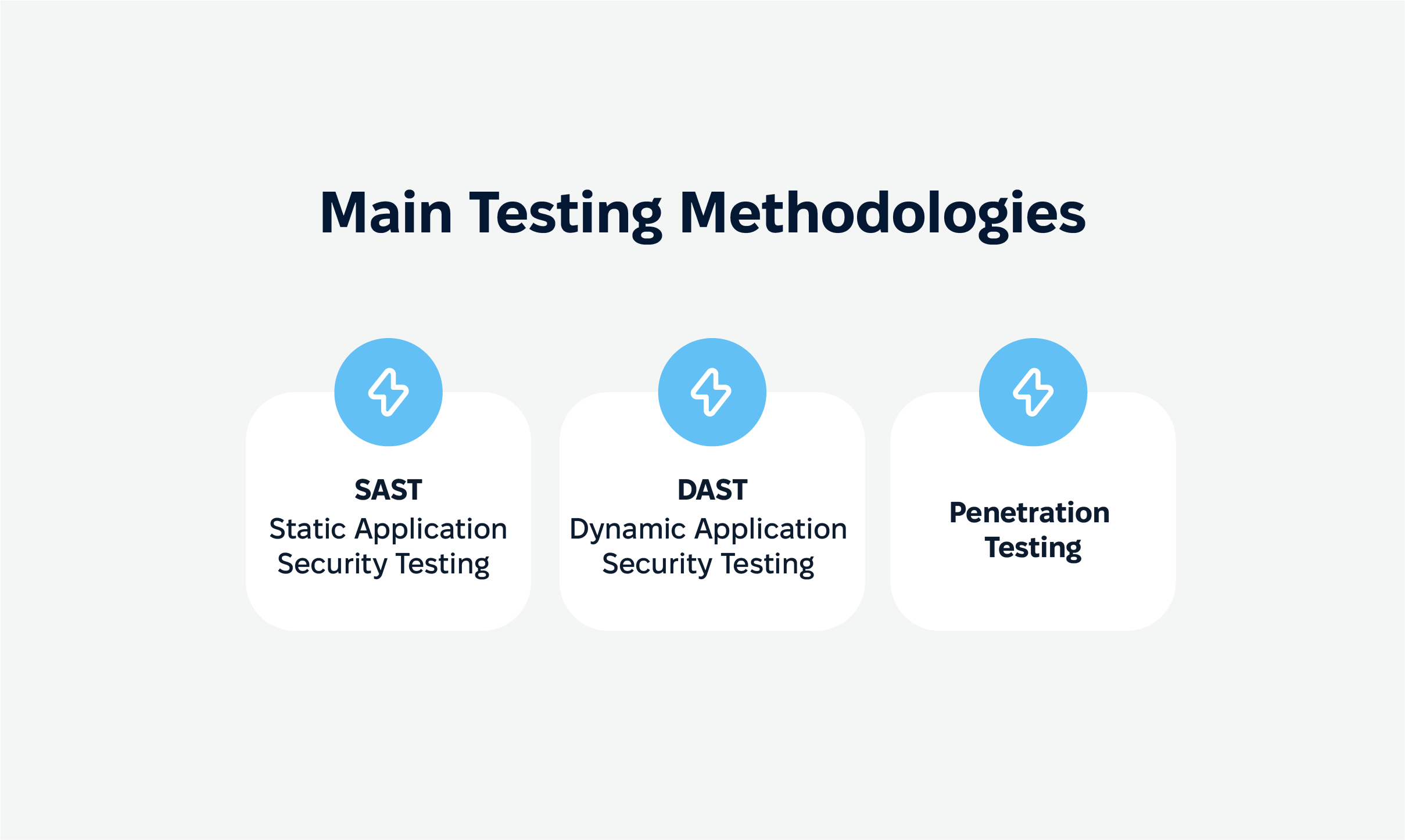
- Static Application Security Testing (SAST). This is some kind of a “pre-flight check” that combs through your source code to catch vulnerabilities before your app even takes off. By scanning for weak spots early in the development process, SAST can help you prevent costly fixes later on.
- Dynamic Application Security Testing (DAST). If SAST is about prevention, DAST is about detection. DAST tests the app in real time, simulating what an attacker might do while the app is running. This method exposes vulnerabilities that only appear when the app is live.
- Penetration Testing. This is the ultimate stress test, where ethical hackers attempt to break into your app to find exploitable weaknesses. This method mimics real-life attack scenarios, showing you exactly how a hacker might attempt to gain unauthorized access to sensitive data.
Validation
In a nutshell, validation is all about confirming that every security measure is functioning as it should.
Validation key elements
- Regular audits – examining the app to ensure it’s up to industry standards, reveal gaps that might otherwise go unnoticed, especially as applications evolve or adopt new features.
- Code reviews to catch errors or insecure coding practices early, making it easier to fix issues before they reach production (ideally, include a mix of manual inspection and automated scanning).
- Pen testing – helpful before major releases or after substantial updates to ensure that recent changes haven’t introduced new security gaps.
Each of these steps is a piece of a larger puzzle. But to stay truly secure, continuous monitoring should complement validation. It enables you to track your app’s security posture in real-time, catching anomalies that might signal potential threats or vulnerabilities.
Common pitfalls
While validation is critical, there are common pitfalls that organizations often encounter:
- Skipping validation during updates. Each update, whether it’s a bug fix or a feature enhancement, can introduce new vulnerabilities. For instance, adding new APIs or integrating third-party services can create security risks if they aren’t thoroughly tested.
- Over-reliance on automation may miss nuanced vulnerabilities that a human reviewer would catch. Striking a balance between automated and manual testing provides a more comprehensive approach to validation.
- Neglecting user permissions and access controls. As new features are added, user roles and permissions often need to be updated as well. Failure to review and adjust access controls can lead to users gaining access to sensitive data they shouldn’t see.
- Infrequent testing. Mobile apps and the threats they face are constantly evolving. Regular testing and re-validation are essential to ensure the app’s security measures remain effective over time.
Tools and resources
- OWASP ZAP. Known for its reliability in DAST, OWASP ZAP is a free, open-source tool that helps identify security flaws in running applications.
- AppScan. With robust capabilities for vulnerability management and scanning, AppScan is ideal for companies needing a comprehensive security testing suite.
- Burp Suite. A popular choice for penetration testing, Burp Suite helps you find security weaknesses by simulating attacks and assessing your app’s defenses.
Mobile App Security Best Practices: Implementation Done Right
Building security into your app is like constructing a solid house. If the foundation is weak, the rest won’t hold. Let’s start with a practical, step-by-step approach to getting security implementation right.
Step-by-step Approach
Step 1. Planning and risk assessment
Start by identifying your app’s biggest security risks. Knowing where potential vulnerabilities lie allows you to focus resources effectively.
Duration: This phase typically takes a few weeks, but it sets the foundation for the entire project.
Step 2. Define security requirements
Based on compliance needs and industry standards, outline your security requirements. This step sets the groundwork for meeting regulations and protecting user data.
Duration: This phase typically takes 1–2 weeks, depending on the complexity of the app and regulatory requirements.
Step 3. Integrate security by design
Instead of tacking security on at the end, build it into your app from the beginning. Secure coding practices, encryption, and strong authentication measures should be woven into the app from the ground up.
Duration: Depending on the complexity of the app, building security into the development process can add several weeks to a typical timeline.
Step 4. Testing and validation
Testing using multiple methodologies like SAST, DAST, and pen testing.
Duration: Comprehensive security testing can add a few weeks to the timeline, but it’s critical for catching vulnerabilities before they reach users.
Step 5. Continuous monitoring
Cybersecurity isn’t a one-time job but a fundamental continuous process. Regular monitoring allows you to catch new vulnerabilities or issues as they arise, keeping your app safe and secure.
Duration: This is a long-term commitment, requiring regular updates and security patches. Budget time for ongoing maintenance because security is never fully “done.
Key players: the dream team for mobile app security
One of the most important mobile app security best practices is forming a team that brings a range of skills and expertise.
- Developers are the architects of app security. They need to adopt secure coding practices from the get-go, staying up-to-date on techniques like encryption, code obfuscation, and vulnerability management.
- From managing server security to ensuring data encryption, IT staff monitor system activity for any suspicious behavior.
- In strictly regulated industries, you’ll need compliance experts to make sure the app complies with all the necessary regulations (optional).
- Security experts, who hunt down vulnerabilities and conduct regular risk assessments. They play a key role in penetration testing, which simulates attacks to see where the app’s weak spots are.
- Project managers who keep everything on track. They coordinate timelines, allocate resources, and ensure that all security tasks are completed without disrupting the overall app development process.
Success factors
The most successful security programs share a few common elements. First – collaboration across departments. A secure app isn’t the sole responsibility of the IT team. Compliance, development, and project management teams should all collaborate to ensure security goals are met.
The second key to success is user awareness. Users also play a part in app security. Educate them on safe usage practices, such as enabling multi-factor authentication and safeguarding their devices.
And last but not least, clear documentation. Documenting security policies and procedures helps ensure everyone on the team is on the same page. Good documentation also provides consistency and a reference point for future audits.
What It’ll Cost You: Budgeting for Mobile App Security
Mobile app security is a serious investment, but it pays off in the long run. To budget effectively, it’s important to understand the main cost factors.
- Application complexity
The more complex an app, the more extensive the security measures needed. High-functionality apps that store or transfer sensitive data will naturally require more security resources.
- Compliance requirements
Compliance with regulations such as HIPAA or GDPR comes with additional costs. For regulated industries, these expenses are non-negotiable, as non-compliance can result in hefty fines.
- Security tools
Quality tools often require a financial commitment. While free tools are available, many companies opt for paid solutions with advanced features and customer support.
ROI and hidden costs
The potential ROI behind app cybersecurity includes avoiding breaches, protecting reputation, and mitigating the risk of regulatory penalties. However, hidden costs can crop up.
For instance, your team members need regular training to stay updated on the latest security practices, and it costs some money. Another common example is a security incident case. However, having a plan and resources in place to address breaches quickly can save significant costs and reputation.
Cost optimization tips
1. Use open-source tools for high-quality security on a budget
Open-source tools like OWASP ZAP, MobSF, etc., are versatile, well-supported, and, best of all, budget-friendly. Many of these tools are developed by the security community and used by professionals worldwide.
2. Leverage cloud-based solutions for built-in security
In this case, you get
- Built-in encryption and compliance as leading cloud providers, such as AWS, Microsoft Azure, etc., offer robust security controls that include data encryption, identity and access management, and compliance certifications (e.g., HIPAA, GDPR, PCI DSS).
- Scalability.
- Managed security services ( automated threat detection, monitoring, and incident response).
3. Automate security processes
- Continuous Integration/Continuous Deployment (CI/CD) pipeline automation.
- Automated vulnerability scanning.
- Automated monitoring and alerts.
4. Focusing on risk-based security
Adopting a risk-based approach can help you prioritize resources for the highest-impact security tasks, especially if your budget is tight.
- Prioritize high-risk areas: login systems, payment processing, and any storage of personally identifiable information (PII), etc.
- Tiered security policies: you might use more intensive monitoring and encryption for sensitive functions while applying lighter security measures in less critical areas.
- Periodic security assessments: targeted testing reduces costs compared to doing continuous full audits but still ensures that critical parts of the app remain secure.
5. Invest in security training for long-term savings
Training might seem like an upfront expense, but it’s actually a cost-saving measure in disguise. When developers and team members understand security basics, they’re less likely to introduce vulnerabilities in the first place. A security-savvy team can help avoid costly fixes down the line.
Conclusion
When it comes to mobile app security, it’s not just about crossing your fingers and hoping for the best. With the rise of threats like smishing, malware, and data breaches, taking the right steps today can save you from a headache tomorrow. For regulated industries like healthcare, finance, and insurance, the stakes are even higher. Think of it like locking your front door – you wouldn’t leave it open for just anyone, would you?
By following best practices like encryption, secure APIs, and strong authentication, you can keep your app safe from cyber threats and stay on the right side of compliance regulations like HIPAA and PCI DSS. Regular testing and monitoring are key to staying ahead of hackers – because, let’s face it, if you’re not checking your app’s security, someone else might be.
So, if you’re ready to turn your app security from “good enough” to “rock solid,” let’s chat! Cadabra Studio’s experts are ready to help you lock down your app with the latest tech and best practices. Don’t wait until it’s too late – get in touch with us today for a consultation. After all, an ounce of prevention is worth a pound of cure!