Web development security best practices are critical to protect against evolving threats. This guide covers key best practices including web development security measures such as input validation and secure coding to prevent vulnerabilities like SQL injection and cross-site scripting, ensuring adherence to web application security standards.
Implementing robust security measures during the development process of a web app is essential to protect users’ data and prevent vulnerabilities.
Key Takeaways
Web application security is essential; integrate security from the start to prevent vulnerabilities like SQL injection and cross-site scripting.
Key practices for web development security include data encryption, secure coding, API security, regular audits, and secure hosting configurations.
Neglecting web application security can cause financial and reputational damage, so proactive measures and awareness of emerging technology trends are crucial.
What is Web Application Security
Web application security involves practices and measures to protect web applications from unauthorized access, attacks, and breaches. It includes various security controls such as authentication and access control, web application firewalls, and secure coding practices to ensure the integrity, confidentiality, and availability of web applications.
Common vulnerabilities in web applications, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), can cause severe consequences like data breaches and financial loss. Understanding these vulnerabilities and applying robust security measures protect web apps from threats.
Dynamic application security testing and penetration testing are important to identify and mitigate security vulnerabilities. Regular testing and review of security measures ensure web applications are secure and resilient against evolving threats.
Key Web Development Security Best Practices
Adopting key web development security best practices protects web applications from potential threats. Proper web server management and configuration are crucial for maintaining security. These practices include data encryption and protection, secure coding practices, API security, regular security audits, and penetration testing, along with secure hosting and server configuration.
Following these best practices ensures the security and integrity of web applications.
Data Encryption and Protection
Data encryption and protection are critical components of web application security. Using encryption protocols like TLS, HTTPS, and AES ensures that sensitive data is protected both at rest and in transit. Encrypting data prevents unauthorized access and safeguards critical data from potential breaches.
Securing data at rest and in transit involves implementing robust encryption techniques and ensuring that sensitive information is stored securely. Adhering to best practices for data encryption and protection mitigates the risk of sensitive data exposure and enhances overall web application security.
Secure Coding Practices
Secure coding practices are essential for preventing common vulnerabilities and ensuring the security of web applications. Input validation and sanitization are crucial techniques for protecting against injection attacks and malicious code. Developers can prevent SQL injection and cross-site scripting attacks by validating user input. Additionally, sanitizing the input is a crucial step in this process.
Preventing SQL injection, XSS, and CSRF attacks requires implementing secure coding practices and following security guidelines throughout the software development lifecycle. Incorporating preventive measures and regularly reviewing security controls ensures the integrity and security of web applications.
Validating User Input
Validating user input is a cornerstone of web application security. It involves scrutinizing the data entered by users to ensure it meets predefined criteria, such as format, length, and content. This process is crucial for preventing malicious data from being processed by the application, which can lead to significant security vulnerabilities.
There are several types of input validation that developers should implement:
Format validation: Ensures that the input data conforms to a specific format, such as a date or email address.
Length validation: Checks that the input data falls within a specified length range.
Content validation: Verifies that the input data contains only allowed characters or values.
To effectively implement input validation, developers can use various techniques, including:
Regular expressions: Utilize regular expressions to match input data against specific patterns.
Validation libraries: Leverage libraries that provide pre-built validation functions for common data types.
Custom validation: Write custom code to validate input data based on specific business rules.
By rigorously validating user input, web applications can thwart common security threats such as:
SQL injection: Malicious input data that manipulates database queries.
Cross-site scripting (XSS): Malicious input data that injects harmful code into web pages.
Implementing robust input validation is a proactive measure to enhance web application security, protecting against a wide array of security vulnerabilities and threats.
API Security
API security is important for web applications that use REST and GraphQL APIs. Securing APIs and implementing authentication and access control will prevent unauthorized access and protect sensitive data. Using API gateways and authentication tokens will strengthen security, ensuring only authorized users can access the APIs.
Implementing robust security measures for APIs, such as transport layer security and multi-factor authentication, will mitigate security vulnerabilities and protect web applications from threats. Following best practices for API security will keep web applications secure.
Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are important to identify and mitigate security vulnerabilities in web applications. Performing vulnerability assessments and dynamic application security testing will detect and address security threats before they lead to a security breach. Regularly testing and reviewing security measures will keep web applications secure.
Conducting security audits and penetration testing involves regularly reviewing known vulnerabilities and implementing security controls to address potential threats. Being proactive with security testing will keep web applications secure.
Secure Hosting and Server Configuration
Choosing secure cloud hosting providers and keeping server software and dependencies up to date is important for web application security. Selecting reputable hosting providers and securely configuring web servers will protect web applications from threats.
Regularly updating server software and dependencies will mitigate security vulnerabilities and keep web applications secure. Following best practices for secure hosting and server configuration will enhance the overall security of web applications.
Exception Management and Error Handling
Exception management and error handling are critical components of secure web development practices. These processes involve:
Handling exceptions: Catching and managing exceptions that occur during the execution of the application.
Error handling: Addressing errors that arise during application execution.
Logging: Recording errors and exceptions to facilitate debugging and security incident response.
By implementing effective exception management and error handling, web developers can achieve several security benefits:
Prevent information disclosure: Ensure that sensitive information is not inadvertently disclosed to unauthorized users.
Prevent security vulnerabilities: Mitigate security vulnerabilities that could be exploited by attackers.
Improve security incident response: Enhance the ability to respond to security incidents by maintaining detailed logs of errors and exceptions.
Incorporating these practices into the development process not only improves the robustness of web applications but also strengthens their overall security posture. By proactively managing exceptions and handling errors, developers can safeguard their applications against potential security threats and vulnerabilities.
Web Development Security Checklist
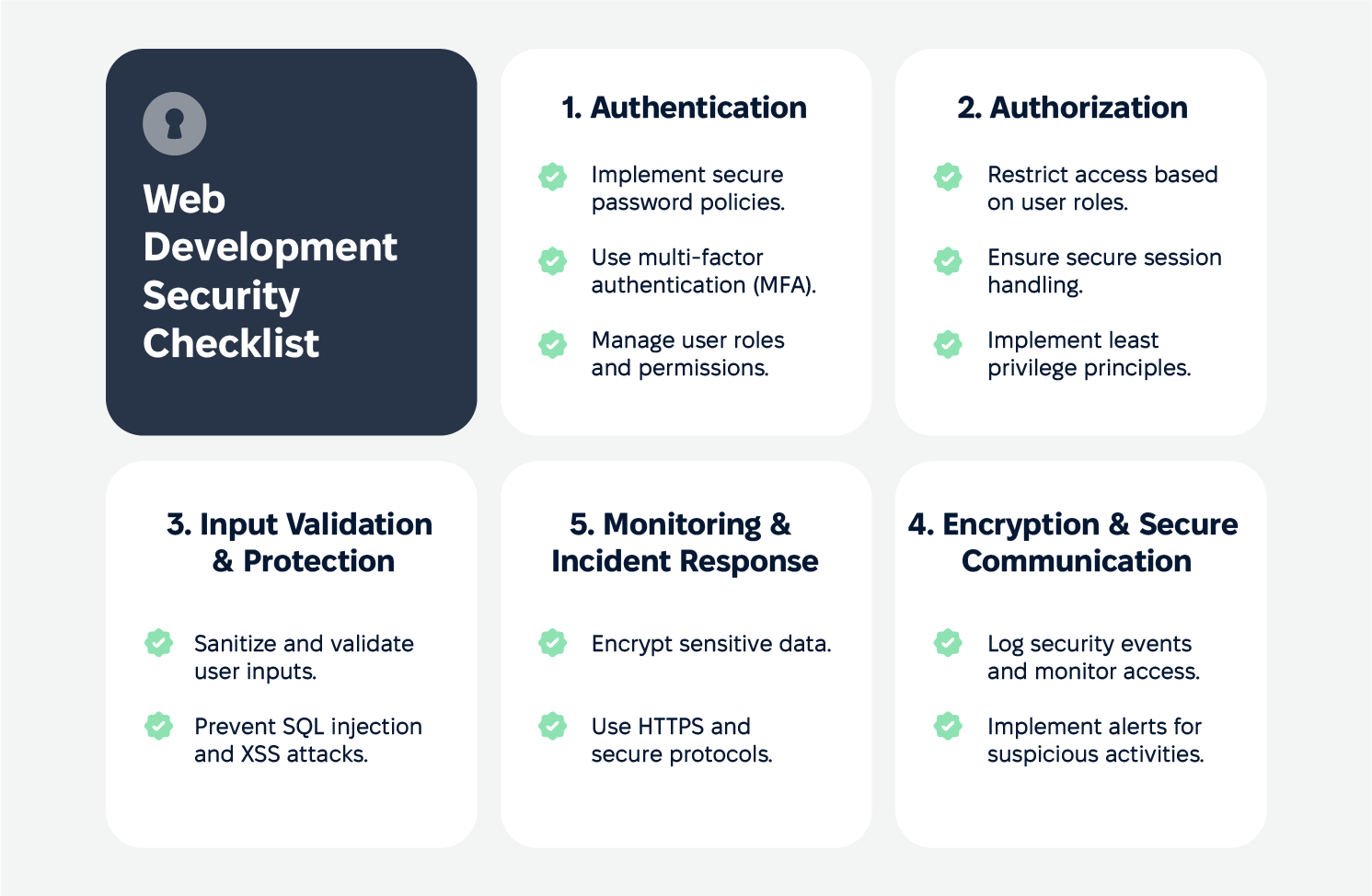
A step-by-step web development security checklist is important for developers and IT teams. This checklist includes implementing authentication and access control, securing user input, and regularly performing vulnerability scanning and dynamic application security testing. Following this checklist will keep web applications secure.
Integrating security into the DevOps pipeline involves implementing security practices throughout the software development lifecycle. Embedding security into the development process will allow developers to address security threats proactively and keep web applications secure.
The Cost of Ignoring Web Security
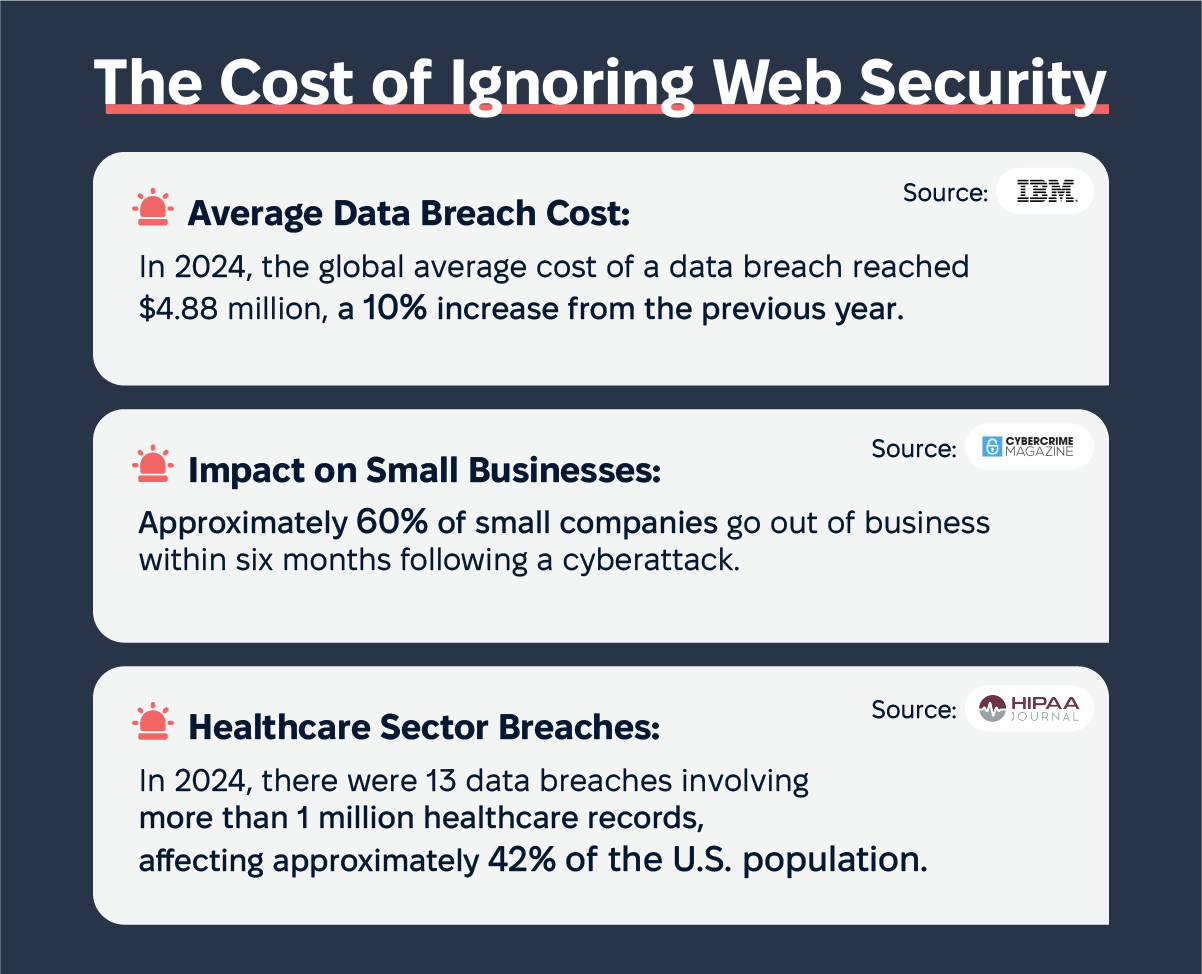
The cost of ignoring web security can be massive for businesses. Case studies of data breaches show the financial and reputational damage caused by security flaws. In 2024, the global average cost of a data breach reached $4.88 million, marking a 10% increase from the previous year (IBM). This highlights the escalating financial risks associated with inadequate web security.
Understanding the impact of a security breach will help businesses prioritize web security and implement proactive measures to protect their applications. Approximately 60% of small companies go out of business within six months following a cyberattack, emphasizing the dire consequences for smaller enterprises (Cybercrime Magazine).
Security flaws can damage a business’s reputation and erode customer trust. Investing in web security and following best practices will help businesses avoid the costly consequences of a security breach and maintain their market reputation. Notably, in the healthcare sector, there were 13 data breaches in 2024 involving more than 1 million healthcare records, affecting approximately 42% of the U.S. population (The HIPAA Journal). This underscores the critical need for robust security measures in safeguarding sensitive information.
Future Trends in Web Development Security
The future of web development security is shaped by emerging technologies and trends. Here are some key points to consider:
AI-powered threat detection is becoming important for web application security.
Zero Trust architecture is gaining traction as a way to improve security.
Leveraging these will allow developers to address security threats proactively and protect their applications.
By staying updated on these, developers can secure their web applications better.
Blockchain is also playing a big role in web security. Integrating blockchain in web applications will enhance security features and data integrity. Staying updated on the future of web development security is important to build secure and resilient applications.
How Cadabra Studio Helps You Build Secure Web Applications
Cadabra Studio offers audit and consultation services to help businesses build secure web applications. Conducting a thorough security audit and following best practices will ensure Cadabra’s web applications comply with security requirements and regulations.
Cadabra Studio’s team will provide valuable insights and recommendations to improve web application security. Partnering with Cadabra Studio will ensure businesses’ web applications are secure and resilient against threats.
Conclusion
Web application security is part of web development. By following best practices like data encryption, secure coding, and regular security audits, developers can protect their applications from threats and data integrity. Staying updated on future security trends and incorporating proactive security is key to building secure and resilient web applications.
Investing in web security is not just a technical requirement but a business requirement. By prioritizing security and following best practices, developers can build secure web applications that build trust and confidence in users.
Need a Security Audit for Your Web Application?
If you want to secure your web applications, explore Cadabra Studio’s secure development services. A web application audit is necessary to identify and address security vulnerabilities before they lead to a security breach.
Cadabra Studio offers a full web application audit that combines white box and black box testing. Using a range of tools and techniques, Cadabra Studio will ensure your web applications are secure and compliant.
Frequently Asked Questions
Why is website security essential?
Website security is crucial to safeguard against unauthorized access and potential damage, ensuring the integrity and availability of the site. Prioritizing website security helps to maintain user trust and protect sensitive information.
How can developers ensure secure coding practices?
Developers can ensure secure coding practices by adhering to best practices for input validation and sanitization, while actively working to prevent common vulnerabilities such as SQL injection and cross-site scripting (XSS). This disciplined approach is crucial for building resilient applications.
What is the importance of regular security audits in web development?
Regular security audits are crucial for identifying and mitigating security vulnerabilities, thereby ensuring the integrity and protection of web applications. Implementing these audits enhances overall security and reduces potential risks.
How does data encryption enhance web application security?
Data encryption significantly enhances web application security by safeguarding sensitive information, ensuring that data remains secure both during transmission and when stored. This protection against unauthorized access is crucial for maintaining data integrity and confidentiality.
What role do secure hosting and server configuration play in web security?
Secure hosting and server configuration are crucial for protecting web applications from potential threats by ensuring that servers are properly configured and regularly updated. This significantly reduces vulnerabilities and enhances overall web security.